What is SPF?
The Problem
When sending emails, anyone can claim to be a sender. i.e. I can claim to be you:
From: your-name
return-path: your-email
Body: Mum I have broken my leg in Timbuktu. Please send
$20,000 to cover my bill. I will repay you when I get home.
It is a common scam.
Case Study - Help me out scam
Our “uncle” Lala (1) (not via blood) fell such a scam:
- He got a message from his pastor.
- The pastor claimed he was stuck in Timbuktu, and needed ₹ 100,000 - 300,000 INR to get out.
- Not a second to waste! Lala did not want to investigate: if he spent a few minutes interrogating and verifying, then someone else could help the pastor, in the intervening time period and steal his glory! Sacre-bleu! He wired the money immediately. And probably chuckling to himself: how he beat everyone to the finish line; he was looking forward to high praise and adulation from members of his congregation. “Look how wealthy he is, he is so generous!” (2).
Case Study - Conveyancing Scams
Your conveyancer emails you details re: the purchase and deposit of your home:
From: your-conveyancer
return-path: your-scammer
Body: Congratulations on purchasing your home! Please transfer your $200k deposit to this bank account: 666-666 666666
You oblige and transfer the money. Usually the conveyancer will call, frantically:
“Why haven’t you transferred the deposit”
“But I have transferred it?” you reply.
“No you didn’t”
“Yes I DID!”
“To what account?” asks the conveyancer.
“To your nominated account: 666-666 666666 “
“Mate, 666-666 666666 is not my account!”
Unfortunately, many home owners are realising that it is too easy to spoof an email address, especially if your email server has very low security protection.
How can we avoid falling into this scam?
Via the SPF protocol.
What does it check? How does it work?
It verifies that the:
- sending email server’s IP address has been authorised by:
- the sender, according to the sender’s DNS server.
The sender adds an “SPF record” with his DNS server. This SPF record lists the IP address of all email servers that are authorised to send emails on behalf of the sender.
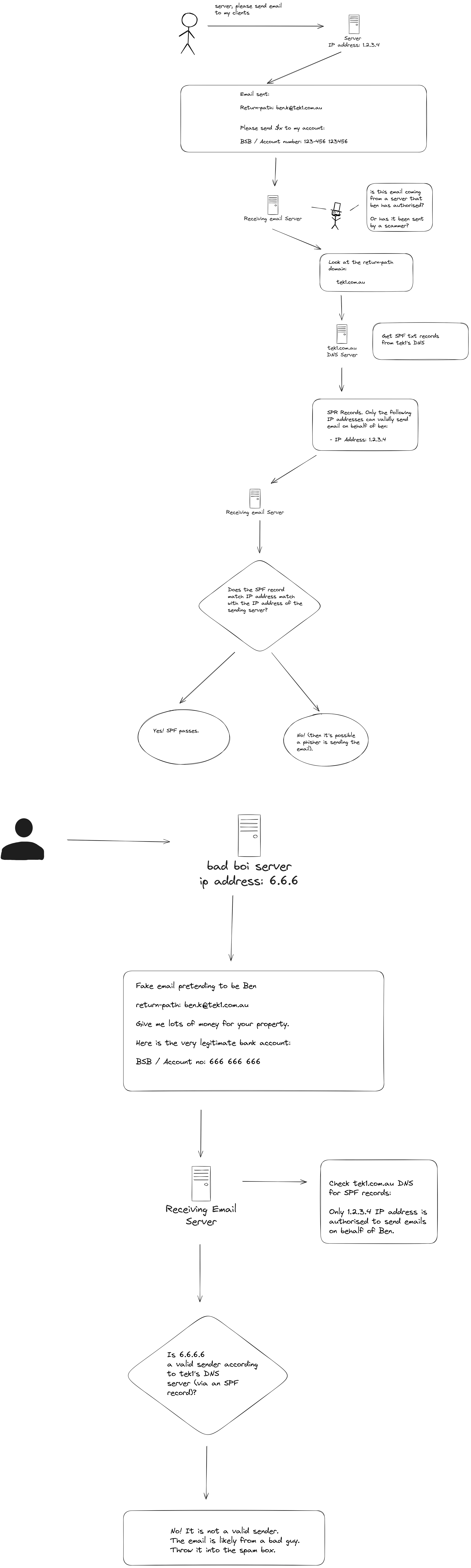
Consider the following work-flow:
- Ben sends an email from server ip address:
1.2.3.4with a return-path address of:ben.k@tek1.com.au - The receiving email server needs to investigate whether
tek1.com.auhas authorised1.2.3.4to send emails. - The receiving email server: asks
tek1.com.au’s DNS server for its SPF records. It will then check whether the SPF records contain a matching1.2.3.4entry. - If the entry does not exist, then the email which has been received ought to be treated with extreme caution. Perhaps it has been sent by an attacker.
Look at the diagram below: right click and open in a new tab:
1 Lala is his pet name, not his legal name.
2 Long experience has taught me, that those who earn their money, legitimately, through hard work: are careful to spend it. But those who spend someone else’s money, or money earned illegitimately: they tend to be flippant. Why should you carefully steward money you didn’t earn? Those who earn by dishonest means tend to lose it quickly, on foolish and ill-founded ventures. Such is the case with our man here.